- HubPages»
- Technology»
- Internet & the Web»
- Viruses, Spyware & Internet Security
How to Remove a Worm or Virus from Your Computer

In the past few months, I have received more phone calls than usual from my friends who are on the verge of hysteria-- "my computer has a virus and it's from the FBI!" The recent attacks from the virus, known as Reventon Ransomeware, promises its victims to free them from the virus (and prosecution) if they pay a fee. After inadvertently downloading the Ransomeware, by Citadel Malware, on their computer, the unsuspecting web surfer is suddenly presented with warning that they have been frozen because of their "illegal activities" on the internet.
The Bogus FBI Virus from Citadel
Although my friends would never do anything to cause an intervention from a legal authority...(okay, maybe), the FBI logo is displayed proudly on their "we locked your computer" page, as well as the information that instructs you to send your payment and be freed from further charges. Although the threats are obviously bogus and not exactly the most convincing proposal of extortion, people infected with the virus are paying their ransoms and hoping to free their computer from the FBI's jurisdiction-- only to find their computer is still behind bars and locked up forever. The scam artists quickly change tactics and move on with no way for anyone to track them. Cybercrime at it's best is a snatch and grab-- then flee!
Reventon Ransomeware
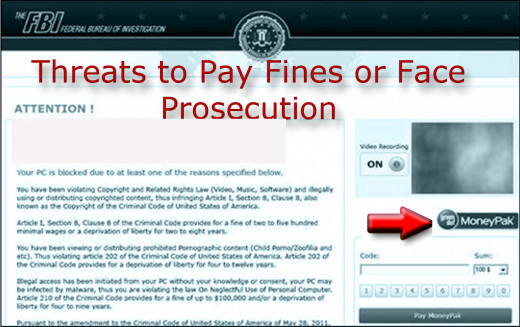
Variations of the Reventon Ransomeware
In addition to the virus being identified by the FBI,some of the similar bogus threats disguise themselves as the Department of Justice’s Computer Crime and Intellectual Property Section, as having been associated with illegal online activity. To unlock their computers, users are required to pay a fine using a prepaid money card service, such as a "moneypack" option that is displayed on the locked screen. It's a despicable act of cybercrime, and these criminals really need to be found by the actual FBI and prosecuted as quickly as possible.
Citadel Malware: Reventon Demands
“The malware lists the fines and penalties for each infraction and instructed me to pay $200 with a MoneyPak debit card purchase. The instructions included how to load the card and make the payment to the FBI. The instructions included that if the payment was not made, criminal charges would be filed and my computer would stay locked on that frozen screen from the FBI.”
The FBI Renounces Blame and Asks You Report the Crime
Called "malware" by the FBI, they have recently put out an official podcast in the response to the barrage of complaints they've received. "We would never ask anyone to pay an online fine to free their computer," says Special Agent Herbert Stapleton. The FBI podcast encourages you to take your computer to a computer professional and asks you to report the crime to the IC3 website.
Steps to Computer Rehabilitation


Unlock Your Computer and Live in a Free Society
Although the Reventon Ransomeware virus is used as an example in this article, you can free your computer from any virus or malware with these steps. The Reventon is very sophisticated, at least I found it challenging to figure out, and most other malicious malware aren't as robust, so you should be able to remove anything from the laptop with these instructions.
Run any Malware or Virus Software you Already have Installed
If you have any malicious removal programs, like windows defender, AVG, Kapersky, or any other programs, turn them loose and let them scan the entire computer directory. If this isn't possible, you may try system restore.
Prepare Your Computer for System Restore
Important: Back up your computer if you recently downloaded a new program. Although your documents, photos and other work will not be affected, your new programs may be removed if you installed them prior to the restore date. In other words, if you loaded a software program on Dec 8th, and you are restoring your system to Dec 2nd, that program will be removed. System restore will not remove anything on your computer with an installation date prior to the restore point.
If you can remember when the virus or worm appeared, go back a few days on the restore point to be sure you get it and kill it!
System Restore Process
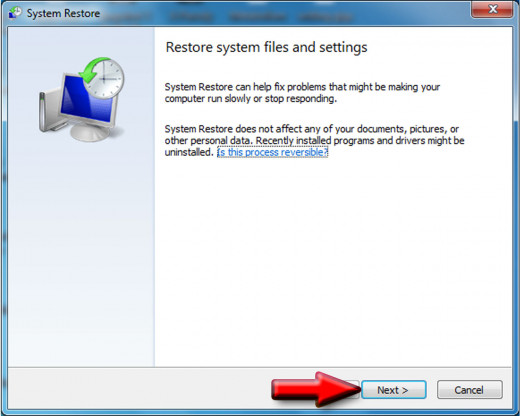
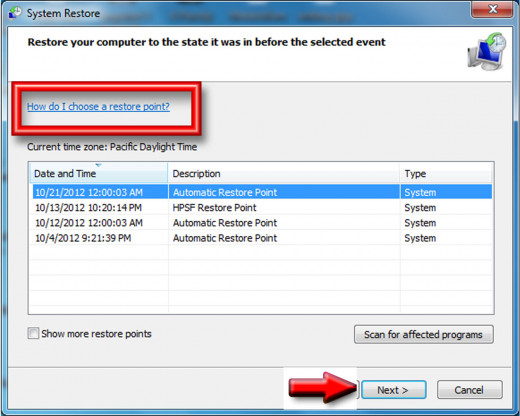
System Restore Complete
Section A: Go to Start, and Type in "System Restore" in the Search Box
For Windows 7 and Vista
In a few moments, System Restore will appear and ask you if your sure you want to do this? Click next. It is better to use the automatic store point if the virus was recent, your computer can detect when something was downloaded--usually a Microsoft Update will trigger the restore point setting--and hit next.
Use Automatic Restore Point
Depending on when the virus, worm or malware appeared, click on the restore point setting and click, Next.
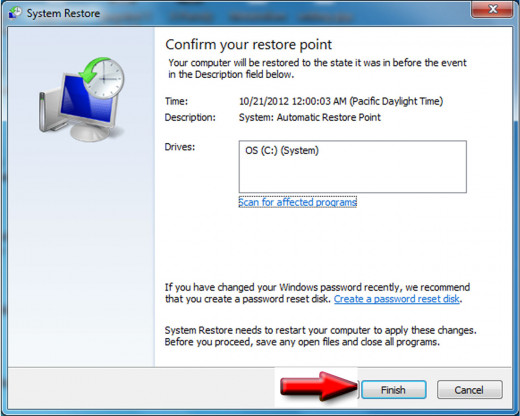
Confirm the Restore Point
After you have selected the Restore Point, the program will ask you to "Confirm" the point and hit, Finish
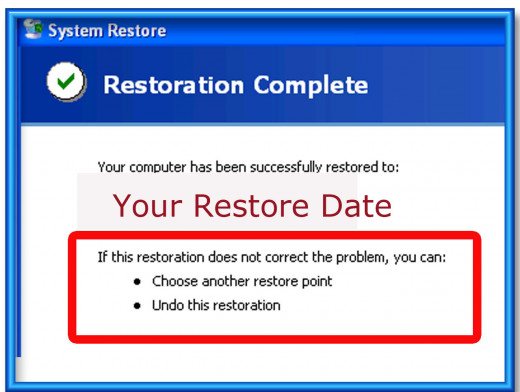
Wait for the Program to Finish the Restore Point
The computer will take some time to process your request and may even close and start again a few times, so don't panic. After the computer has finished and has rebotted, sign in and ensure the computer is cleaned of viruses or malware. If not, you may have not gone back far enough on the restore point, and you may want to try again with a different restore date.
Once the Restore Date is Completed, the Restore Point may be Reversed
Don't worry, you can restore the past on your computer, but chance are you won't want to. If you cannot get into System Restore, you will have to use the Safe Mode to get into the program and turn back the hands of time. Once in Safe Mode, follow the instructions in this section to restore your computer to a working machine. Follow the instructions below to get into Safe Mode through an alternate route.
You May Need to Go Into Safe Mode

How to get into Safe Mode
Section B: What if the Virus won't let me in System Restore?
Citadel malware, the one responsible for Reventon Ransomeware, may not allow you into System Restore to wipe it out. Unfortunately, this designer malware is very sophisticated. But, you can get them. Don't Panic, and follow these instructions to free your machine.
You will have to go into Safe Mode to bypass the Virus
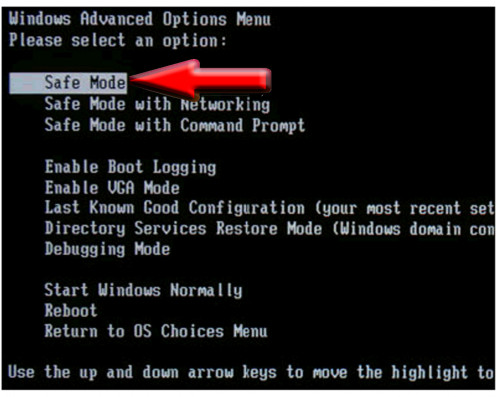
1. Restart your computer and tap on the F8 key until the Windows Advanced Options Menu comes up on the screen.
2. Use the arrow keys to choose Safe Mode and hit enter.
Your Computer is Now in Safe Mode
The Icons will look different, they may be larger or skewed on the screen because the usual drivers and files were not used to load the computer.
3. Type in System Restore in the Search Window and Follow the Steps Provided in Section A of this article.
After you have completed the restore point, your computer should be free of any malware, viruses or worms you have downloaded after that date. However, if your computer is running slow, showing signs of disobedience or has other problems that may be attributed to malicious downloads, you need to update or install better software that will protect you. Free antiviral programs are available if you're in a crunch for bucks ( who isn't?) and many do a great job, although you may have to put up with their ads and pop-ups.
Protect Yourself with Up-to-Date Antiviral Software
Be sure you have a good protection program because new and improved viruses and malware programs are showing up all the time. To keep your computer safe, ensure you are well protected in this age of ever increasing cybercrime.
System Restore at a Glance
For Windows 7 and Vista
| Action
| Purpose
|
|---|---|---|
Restart Computer and tap F8 until the Advanced Menu appears
| Use arrow keys to choose SAFE MODE option
| This Mode bypasses the usual drivers and programs that have been blocked by the virus
|
Sign in and t type "System Restore" in search box under START MENU
| Wait for System Restore to load, it may take a few moments
| You are going to restore the computer programs and files to a date before the virus loaded
|
Choose a Restore Date
| Hit "Next" and wait for the next screen
| Ensure the date you choose for restore is before the day the virus appeared
|
Confirm the Restore Point
| Hit "Next" on the System Restore Menu
| Wait for System Restore to complete
|
Computer will restart on its own
| Sign in and check for the removal of the virus
| If the virus is still on your machine, retry the System Restore with a date further in the past
|